In application security, prioritizing vulnerabilities often feels like finding a needle in a haystack. Traditional methods produce numerous false positives, overwhelming development teams and distracting them from genuinely exploitable threats. Konvu solves this challenge by focusing on the runtime context of your Java applications to accurately pinpoint exploitable vulnerabilities.
What Konvu Does
Konvu leverages runtime context captured from your CI/Test/Staging environments to verify whether vulnerable dependencies are actively used and if vulnerable methods are executed. This strategy ensures your remediation efforts concentrate only on the approximately 5% of vulnerabilities that pose real threats, significantly enhancing security efficiency.
How Konvu Works
Konvu utilizes Java's powerful instrumentation API through an easy-to-use Agent:
-
Dependency Detection
At application startup, the Agent analyzes your classpath and Maven build metadata (found in META-INF within your application JAR) to identify dependencies. Note: Gradle builds are not currently supported. -
Vulnerability Analysis
The identified dependencies are reported to the Konvu backend, which responds with methods known to be vulnerable.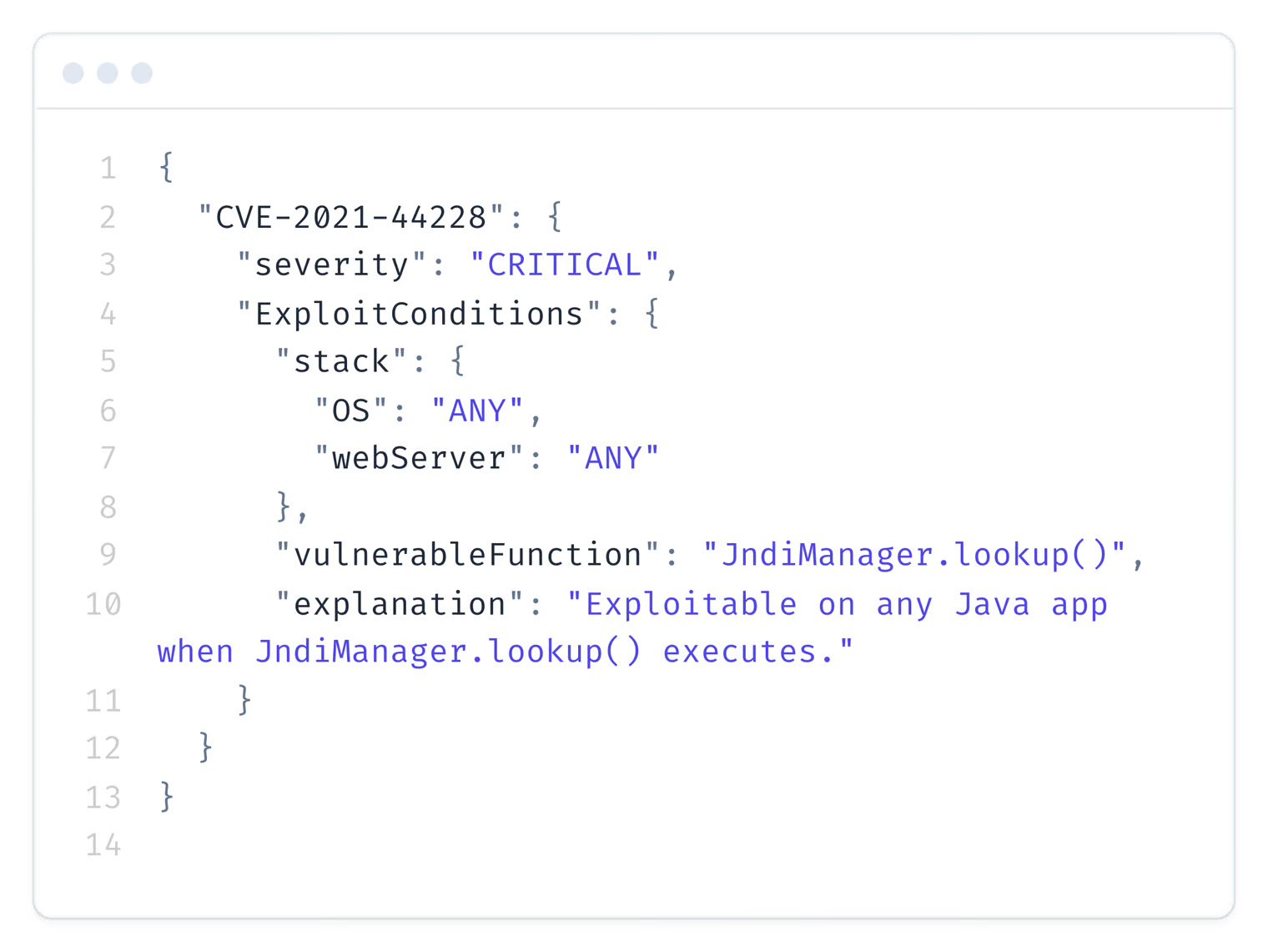
-
Runtime Instrumentation
The Agent instruments only these vulnerable methods, monitoring their execution at runtime.
When a vulnerable method is called, it signals genuine exploitability. -
Contextual Reporting
The Agent periodically sends data to Konvu's backend, including how often vulnerable functions are invoked and detailed call stack contexts, enabling precise correlation with your codebase.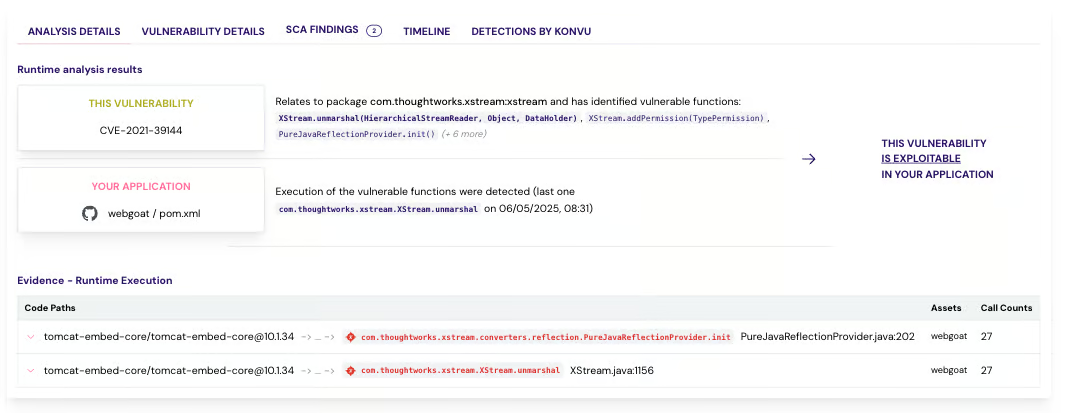
Seamless Installation and Integration
Deploying the Konvu Agent requires no code changes:
- Kubernetes: An available Helm chart automates agent integration into Kubernetes environments.
- AWS ECS: Similar automation instructions ensure straightforward deployment.
- CI Environment: You can even leverage the agent during your CI pipeline's unit test phase if staging or production deployment isn't feasible.
- Compatibility: The Konvu Agent plays nicely alongside other Java agents, including Datadog or Elastic APM, facilitating smooth integration into your existing observability stack.
Minimal Impact on Application Performance
The Konvu Agent is designed with minimal overhead in mind:
- CPU Usage: Negligible overhead, ensuring your application performance remains unaffected. Unlike APMs/Profilers, Konvu's sensor only instruments vulnerable functions and has therefore minimal footprint.
- Memory Footprint: The Agent maintains a lightweight profile post-startup. Initial dependency scanning causes transient overhead at startup but quickly stabilizes, ensuring efficient resource use throughout your application lifecycle.
Compared to eBPF-based Agents
While eBPF offers powerful system-level observability, it presents challenges for in-depth application security analysis compared to Konvu's Java instrumentation:
- eBPF agents often lack the ability to easily access detailed application-level context.
- Probe support across diverse programming languages remains limited.
- Sampling-based eBPF approaches can provide an incomplete view of application behavior, potentially missing critical invocations of vulnerable functions.
We will explore these limitations and comparisons in more detail in an upcoming blog post.
Conclusion
By leveraging runtime context and smart instrumentation, Konvu ensures your security efforts focus solely on actionable vulnerabilities. This approach dramatically improves your application's security posture, saving valuable development resources and enabling teams to rapidly address genuine risks.